Monitoring user’s activity with auth logs
It is common knowledge that the one, who owns information, owns the world. When it comes to business, prompt access to the needed data cannot be overestimated. If you’ve ever encountered yourself in a situation, when you need information about the users’ activity within your CRM system, then this article may be useful for you.
To track the authorized users, their IP Address and time when they logged in, just go to Administration > Auth Log.
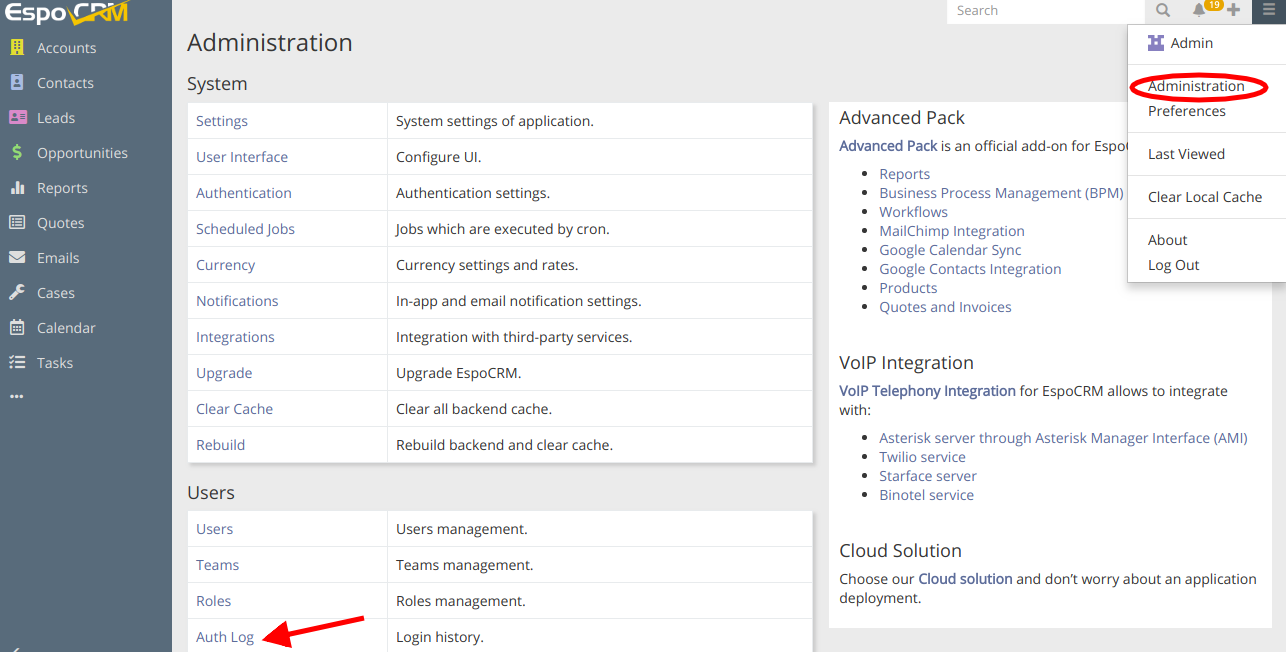
With a few clicks, you will be able to find here detailed information about logged in users, their actions and even remove a log record if needed. You can also track the attempts of unauthorized access and the IP addresses of those who tried to do it, which in turn will help you to ensure your data security.
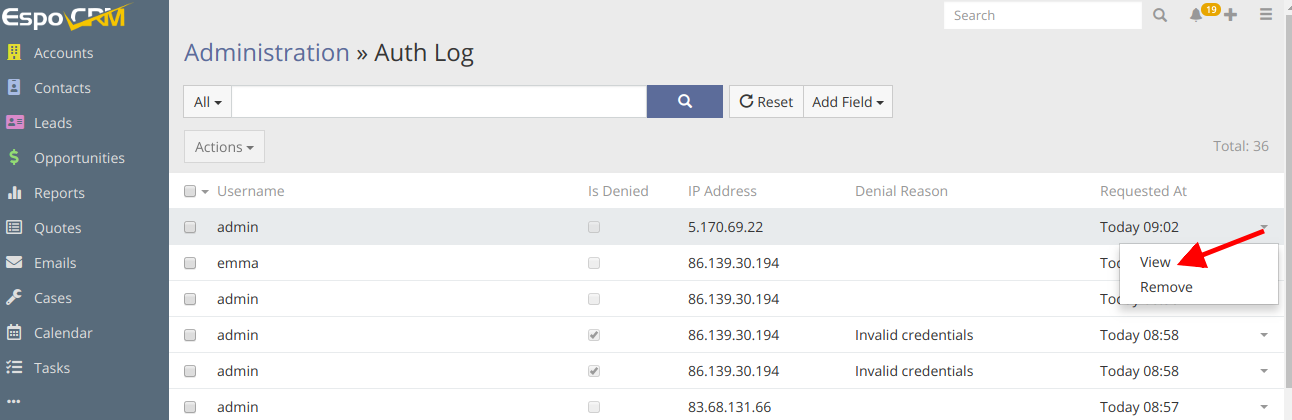
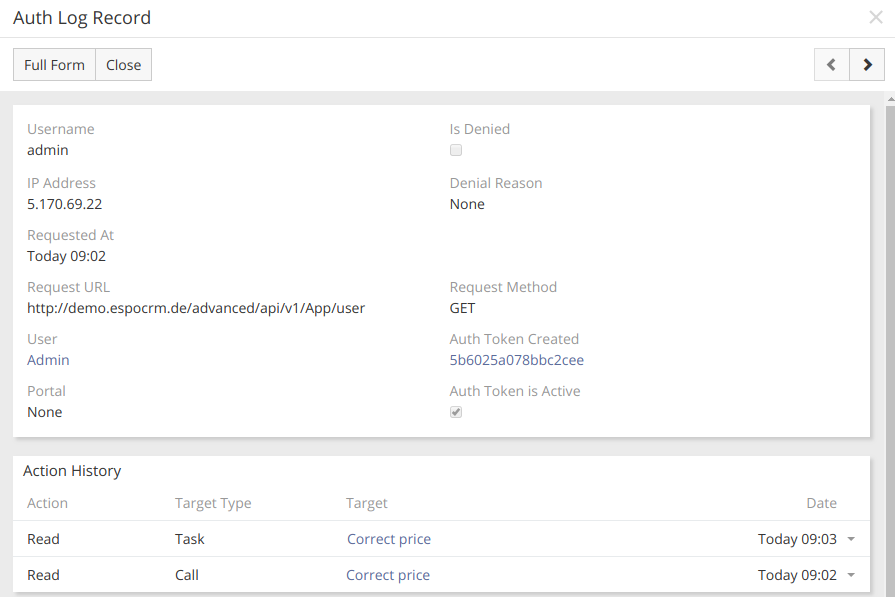
Hope the information was useful for you! Thanks for paying attention!
